A Twitter account known as DarkWebInformer has claimed that a notorious hacker, identified only by the alias “888,” has allegedly…
Cluster Bravo, despite its brief initial activity, subsequently targeted 11 organizations in the same region, as researchers found that these…
September 13, 2024 – Car manufacturer Ford Motor Company has filed a patent application for an in-vehicle advertisement presentation system…
A survey of IT and networking professionals has found that almost all (97%) of them feel that the use of…
India’s Central Bureau of Investigation (CBI), acting on a tip-off by the U.S. Federal Bureau of Investigation (FBI), has dismantled…
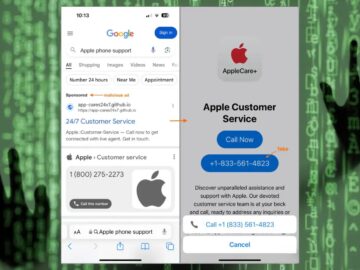
A malicious campaign targeting Mac users seeking support or extended warranty services through AppleCare+ has been uncovered. This scam involves…
In an era where digital threats are evolving rapidly, cybersecurity has become a critical concern for individuals and organizations alike….
Artificial Intelligence (AI) permeates every single industry vertical. In Health, there are abundant opportunities to introduce AI to both clinical…
Microsoft End of Support for Windows 10 Microsoft has announced that it will cease providing security updates for Windows 10…
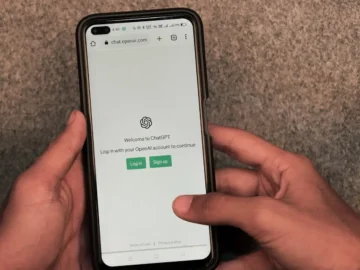
A hacker identified as Amadon has demonstrated a ChatGPT hack, revealing how the AI can be manipulated to produce dangerous…
Cybersecurity researchers have warned of ongoing phishing campaigns that abuse refresh entries in HTTP headers to deliver spoofed email login…
EchoStrike is an open-source tool designed to generate undetectable reverse shells and execute process injection on Windows systems. “EchoStrike allows…