Desktop virtualisation is not a new concept, but IGEL, which recently moved out of the hardware business, is now partnering…
Coinbase cryptocurrency exchange platform has disclosed that an unknown threat actor stole the login credentials of one of its employees…
Abstract: Ransomware is a type of revenue-generating tactic that cybercriminals utilize to improve their income. Businesses have spent billions of…
If an organization relies on automation and tools to highlight API security issues, it is still up to a trained…
Unknown malware presents a significant cybersecurity threat and can cause serious damage to organizations and individuals alike. When left undetected,…
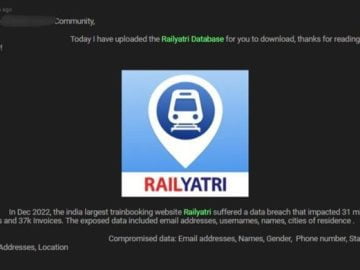
The cybersecurity posture of Indian Railways is under scrutiny again, with the latest breach at the e-booking services website RailYatri….
The finalists for the iTnews Benchmark Awards Best Health Project demonstrate the essential role of information technology in improving the…
Despite economic volatility and tighter budgets, adoption of software as a service (SaaS) continues to increase. Gartner forecasts a 16.8%…
TikTok’s meteoric rise to fame has made it a cultural phenomenon, with over 500 million active users consuming content on…
Microsoft will limit chat sessions on its new Bing search engine powered by generative artificial intelligence (AI) to five questions…
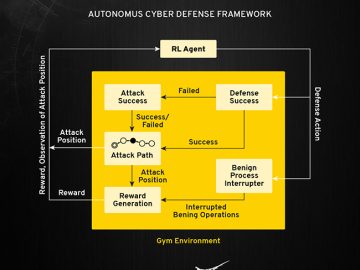
Scientists have taken a key step toward harnessing a form of artificial intelligence known as deep reinforcement learning, or DRL,…
In July 2021, joint research from Enterprise Strategy Group (ESG) and the Information Systems Security Association (ISSA) found the area…