14 Sep Why Your Online Privacy And Safety Will Be Casualties When We No Longer Use Cash Posted at 09:09h…
Ivanti Cloud Service Appliance flaw is being actively exploited in the wild Pierluigi Paganini September 14, 2024 Ivanti warned that…
After Apple’s product launch event this week, WIRED did a deep dive on the company’s new secure server environment, known…
It’s the same story we’ve heard a thousand times: In today’s digital landscape, risk is constantly rising. Cyber threats are…
In a recent interview with The Cyber Express on the show Security Pill, Manish Chachada, Co-Founder and COO of Cyble,…
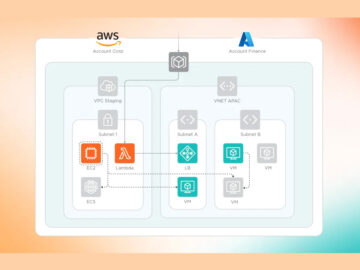
Pioneering Zero Trust Segmentation for Comprehensive Cybersecurity by Samridhi Agarwal, Master’s Student, CMU In today’s rapidly evolving cybersecurity landscape, organizations…
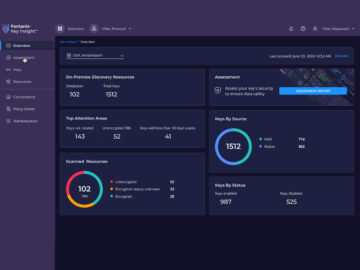
Unveiling Secure Data Practices in a World of AI Risks by Samridhi Agarwal, Master’s Student, CMU In an era where…
A Comprehensive Guide As with many other fields in technology, cybersecurity is in a constant state of evolution. One often…
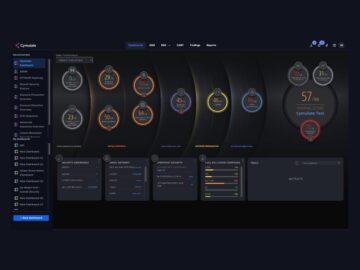
AI Copilot: Revolutionizing Threat Exposure Validation by Samridhi Agarwal, Master’s Student, CMU During BlackHat, Cymulate, a leader in security and…
Despite the vulnerabilities of proximity technology, many organizations have yet to take steps to transition to more secure credentialing systems….
GitLab fixed a critical flaw in GitLab CE and GitLab EE Pierluigi Paganini September 14, 2024 GitLab addressed multiple vulnerabilities…
Sep 14, 2024Ravie LakshmananEnterprise Security / Threat Intelligence Ivanti has revealed that a newly patched security flaw in its Cloud…