Image: MidjourneyPort of Seattle, the United States government agency overseeing Seattle’s seaport and airport, confirmed on Friday that the Rhysida…
Transport for London (TfL) says that all staff (roughly 30,000 employees) must attend in-person appointments to verify their identities and…
Meta is once again making headlines as it pushes forward with its generative AI plans, leveraging public content from UK…
Nuclei scans stuff for vulnerabilities. What does it scan? Modern applications, infrastructure, cloud platforms, and networks. How does it work?…
DNA testing giant 23andMe has agreed to pay $30 million to settle a lawsuit over a data breach that exposed…
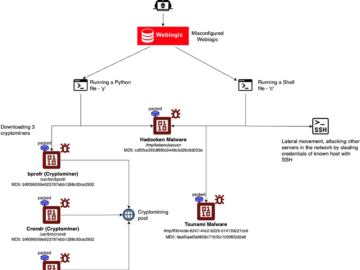
New Linux malware called Hadooken targets Oracle WebLogic servers Pierluigi Paganini September 13, 2024 A new Linux malware called Hadooken…
Hackers are targeting Oracle WebLogic servers to infect them with a new Linux malware named “Hadooken, which launches a cryptominer and…
GraphQL vs REST APIs Developers are constantly exploring new technologies that can improve the performance, flexibility, and usability of applications. GraphQL…
Ivanti confirmed on Friday that a high-severity vulnerability in its Cloud Services Appliance (CSA) solution is now actively exploited in…
Car manufacturer Ford Motor Company has filed a patent application for an in-vehicle advertisement presentation system based on information derived…
Allison’s commitment to neo-fascism and white supremacy appears to have run deep—“I won’t quit til I’m dead. my only goal…
A new Android malware called Trojan Ajina.Banker is targeting Central Asia – Discover how this malicious malware disguises itself as…