The evolution of network security mirrors the broader technological landscape: a journey from simplicity to complexity, from reactive to proactive…
The discussion, featuring Beenu Arora, CEO and Co-Founder of Cyble, examined the potential impact of this acquisition on businesses and…
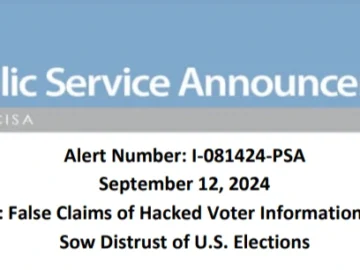
The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) have highlighted a growing concern about…
Docker has addressed critical vulnerabilities in Docker Desktop that could allow attackers to execute remote code. These vulnerabilities, identified as…
Here’s a look at the most interesting products from the past week, featuring releases from Druva, Huntress, Ketch, LOKKER, Tenable,…
Sep 13, 2024Ravie LakshmananEnterprise Security / Vulnerability Cybersecurity researchers have uncovered a new malware campaign targeting Linux environments to conduct…
Mastercard, a leading financial institution renowned for its payment solutions, has significantly strengthened its position in the field of cybersecurity…
Organizations must reassess their email security posture as incidents continue to escalate, leading to financial losses. Key findings reveal a…
Fortinet, a leading cybersecurity firm, has confirmed a data breach involving a third-party cloud service after a hacker, known by…
Infrastructure as Code (IaC) has become a widely adopted practice in modern DevOps, automating the management and provisioning of technology…
SquareX has been named a winner of the prestigious Rising Star category in CybersecAsia Readers’ Choice Awards 2024 Awards, due…
SquareX has been named a winner of the prestigious Rising Star category in CybersecAsia Readers’ Choice Awards 2024 Awards, due…