Alert for Software Developers: North Korea’s Lazarus Group Targets with Malicious Emails A recent study by ReversingLabs has revealed that…
We’ve uncovered a malicious campaign going after Mac users looking for support or extended warranty from Apple via the AppleCare+…
Kubernetes deployments offer plenty of advantages to enterprises that want to update their infrastructure and move to a cloud-native architecture….
Transport for London (TfL) has determined that the cyberattack on September 1 impacts customer data, including names, contact details, email addresses,…
A threat actor claimed unauthorized access to a third-party cloud-based file-sharing service used by Fortinet. The incident reportedly affected several…
Exploiting memory corruption vulnerabilities in server-side software often requires knowledge of the binary and environment, which limits the attack surface,…
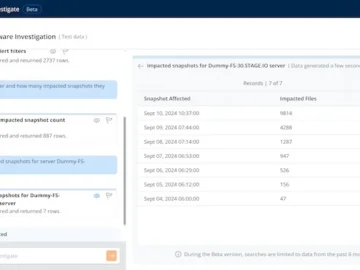
Druva launched Dru Investigate, a gen AI-powered tool that guides data security investigations using a natural language interface. With Dru…
Facebook has admitted that it scrapes the public photos, posts and other data from the accounts of Australian adult users…
Liberal Democrat peer Lord Clement-Jones has introduced a private members’ bill to regulate the use of artificial intelligence (AI), algorithms…
A 17-year-old male was arrested in Walsall following a major cyberattack on Transport for London (TfL), the agency responsible for…
GitLab has released critical updates to address multiple vulnerabilities, the most severe of them (CVE-2024-6678) allowing an attacker to trigger pipelines…
The cybersecurity landscape in 2024 has been marked by a significant surge in malware and vulnerabilities. The Key trends include…