Lazarus Group is a notorious APT hacker group believed to be state-sponsored by North Korea, primarily linked to the country’s…
Sep 12, 2024The Hacker NewsThreat Intelligence / Cybercrime Cato CTRL (Cyber Threats Research Lab) has released its Q2 2024 Cato…
The Indian Computer Emergency Response Team (CERT-In), functioning under the Ministry of Electronics and Information Technology, has issued a high-severity…
Threat actors often exploit legitimate software for malicious purposes as it enables them to evade security measures and gain unauthorized…
Phishing remains a significant concern for both individuals and organizations. Recent findings from ThreatLabz have highlighted the alarming prevalence of…
Every type of fraud is on the rise, and 2023 was a particularly devastating year for victims of cryptocurrency and…
Kyndryl’s latest State of mainframe modernisation report has found that organisations can achieve as much as a 225% return on…
GitLab has released critical patch updates across its Community Edition (CE) and Enterprise Edition (EE) to address security vulnerabilities and…
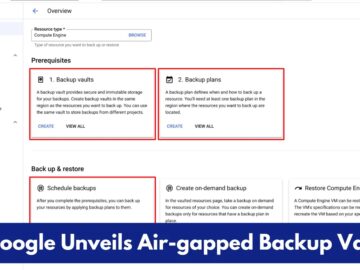
Google Cloud has introduced air-gapped backup vaults as part of its enhanced Backup and Disaster Recovery (DR) service. This new…
The GAZEploit attack consists of two parts, says Zhan, one of the lead researchers. First, the researchers created a way…
SCATTERED SPIDER, a ransomware group, leverages cloud infrastructure and social engineering to target insurance and financial institutions by using stolen…
As ransomware attacks become increasingly sophisticated, hackers are now targeting not just application servers but also their backup systems. This…