That level of diversity demand support from partners with the skills to match, including during periods of migration. According to…
Ivanti has fixed a maximum severity vulnerability in its Endpoint Management software (EPM) that can let unauthenticated attackers gain remote…
Ivanti has issued security updates for its Endpoint Manager (EPM) 2024 and 2022 SU6 versions, addressing several critical and high-severity…
Groundbreaking technology integrates Post-Quantum Cryptography and SSL security for the next generation of Face-based eID solutions and Face-protected Digital Public…
LOKKER released a new consent management solution available in its Privacy Edge Platform. This builds on LOKKER’s earlier release of…
Amazon Web Services (AWS) has pledged to invest £8bn between now and 2028 in the development and maintenance of new…
The Maltese government is working to create a legal framework that supports ethical hacking practices, Prime Minister Robert Abela announced….
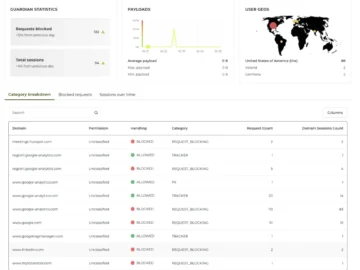
Nine Entertainment blocked up to 96 million web requests from bots and potentially malicious traffic during this year’s Paris Olympics….
Microsoft says this month’s Patch Tuesday cumulative updates also fix a known issue causing Windows Server 2019 boot problems, freezes,…
Cybersecurity researchers at Natto Thoughts recently discovered that Chinese hackers have been actively abusing open-source tools like Nmap to launch…
Microsoft Corp. today released updates to fix at least 79 security vulnerabilities in its Windows operating systems and related software,…
As cyber threats grow, small to medium-sized businesses (SMBs) are disproportionately targeted. According to the recent Hiscox annual cyber readiness…