Microsoft September 2024 Patch Tuesday addresses 79 security vulnerabilities, including four actively exploited zero-days. It covers critical flaws in Windows…
Under the leadership of Prime Minister Narendra Modi and the Bharatiya Janata Party (BJP), the Indian government is preparing to…
September 2024 Patch Tuesday is here and Microsoft has delivered 79 fixes, including those for a handful of zero-days (CVE-2024-38217,…
The threat actor known as CosmicBeetle has debuted a new custom ransomware strain called ScRansom in attacks targeting small- and…
Andrew Phillips has worked at broker LMAX for 17 years and is currently the company’s chief technology officer (CTO). His…
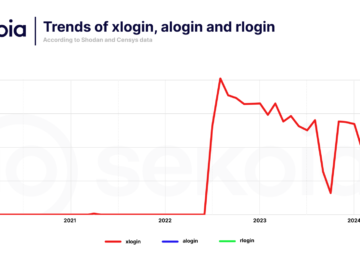
Researchers have closely monitored the Quad7 botnet (also referred to as the 7777 botnet), a notorious cybercriminal group observed to…
NAB has decommissioned its 11-year-old Tableau environment as part of a continued move to a new data platform that it…
Quad7 botnet evolves to more stealthy tactics to evade detection Pierluigi Paganini September 10, 2024 The Quad7 botnet evolves and…
Take Precision to the Next Level—Beyond Basic AI Efficiency and precision are critical in every operation. However, many security teams…
Microsoft announced that Windows 11 installs reaching the end of support next month, on October 8, will be force-upgraded to…
The Slim CD, Inc., a prominent payment processing gateway for US and Canadian merchants, has disclosed a data breach affecting…
Three Chinese state-backed threat groups, APT10, GALLIUM, and Stately Taurus, have repeatedly employed a modified version of the open-source network…