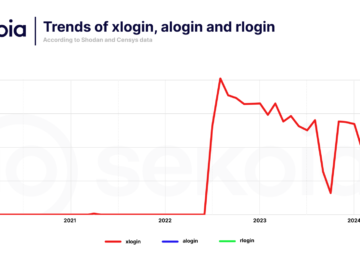
Quad7 botnet evolves to more stealthy tactics to evade detection Pierluigi Paganini September 10, 2024 The Quad7 botnet evolves and…
Take Precision to the Next Level—Beyond Basic AI Efficiency and precision are critical in every operation. However, many security teams…
Microsoft announced that Windows 11 installs reaching the end of support next month, on October 8, will be force-upgraded to…
The Slim CD, Inc., a prominent payment processing gateway for US and Canadian merchants, has disclosed a data breach affecting…
Three Chinese state-backed threat groups, APT10, GALLIUM, and Stately Taurus, have repeatedly employed a modified version of the open-source network…
Cary, North Carolina, September 10th, 2024, CyberNewsWire As cyber threats grow, small to medium-sized businesses (SMBs) are disproportionately targeted. According…
Cary, North Carolina, September 10th, 2024, CyberNewsWire As cyber threats grow, small to medium-sized businesses (SMBs) are disproportionately targeted. According…
Payment provider Slim CD has disclosed a security incident that may have exposed the full credit card information of anyone…
Human-machine understanding (HMU) represents the next frontier in human-centric technology. By integrating insights from human behavioural data, cognitive science and…
AI is significantly evolving penetration testing by enhancing automation, accuracy, and adaptability. AI-driven tools can simulate sophisticated attack techniques, analyze…
If you use the Internet, online privacy should be a growing concern as individuals share more personal information on various…
Ketch launched its product suite for digital media brands. The digital media industry faces increasing challenges. Intense FTC scrutiny on…