09 Sep Cybercrime Magazine YouTube Channel Exceeds 100,000 Subscribers Posted at 09:11h in Blogs by Di Freeze This week in…
This week on the Lock and Code podcast… On August 24, at an airport just outside of Paris, a man…
Sep 09, 2024The Hacker NewsData Protection / Threat Detection The proliferation of cybersecurity tools has created an illusion of security….
A series of vulnerabilities in products made by backup and recovery software supplier Veeam, which were disclosed and patched on…
Couple of men arrested in August 2024 for their alleged role in running a cybercrime forum WWH-Club, which focused on…
Recent research by Cyble Research and Intelligence Labs (CRIL) has revealed a new phishing campaign that capitalizes on the popularity…
South Korea has convened an international summit seeking to establish a blueprint for the responsible use of artificial intelligence (AI)…
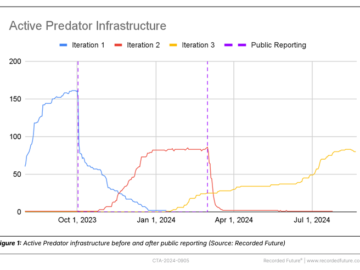
Predator spyware operation is back with a new infrastructure Pierluigi Paganini September 09, 2024 Researchers warn of a fresh cluster…
A privacy flaw in WhatsApp, an instant messenger with over 2 billion users worldwide, is being exploited by attackers to…
GeoServer is an open-source server for sharing geospatial data, and this open-source software server is written in Java. It publishes…
As cybersecurity threats continue to evolve in the ever-changing cyber landscape, organizations within every industry must implement a comprehensive security…
An All-encompassing Approach to Prevent Breaches Organizations depend deeply on technology and data to run their businesses. The recent transition…