Sep 06, 2024Ravie LakshmananSoftware Security / Hacking Threat actors have long leveraged typosquatting as a means to trick unsuspecting users…
AWS S3 (Simple Storage Service) buckets are a popular storage service used by software companies and organizations to store public…
After Office 2024 launches in October, Microsoft will disable ActiveX controls by default in Word, Excel, PowerPoint, and Visio client…
Google, the dominant force in web search, retains your search history whether you approve or not. Many users question the…
Sep 06, 2024Ravie LakshmananCryptocurrency / APT Attack A recently disclosed security flaw in OSGeo GeoServer GeoTools has been exploited as…
A new Android malware named SpyAgent uses optical character recognition (OCR) technology to steal cryptocurrency wallet recovery phrases from screenshots…
Longstanding Darktrace CEO Poppy Gustafsson has announced she is to step down from her post effectively immediately, and will be…
The US Department of Justice has named five Russian computer hackers as members of Unit 29155 – i.e., the 161st…
SonicWall is warning that a recently fixed access control flaw tracked as CVE-2024-40766 in SonicOS is now “potentially” exploited in attacks,…
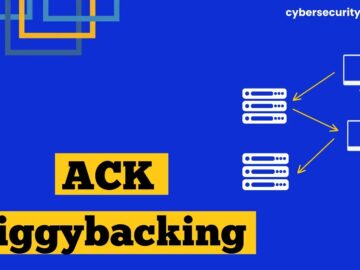
Piggybacking is a term relevant to computer networking and cybersecurity. It describes techniques that aim to optimize data transmission and,…
The spy agency that dared not speak its name is now the Joe Rogan of the SIGINT set. And the…
06 Sep Unfilled Cybersecurity Jobs Can Lead To Utter Chaos Posted at 09:03h in Blogs by Di Freeze This week…