For years, securing a company’s systems was synonymous with securing its “perimeter.” There was what was safe “inside” and the…
The United States District Court for the District of Columbia has today (3 October) unsealed a civil action brought by…
If your organization is like many, your employees may be relying on weak or easily guessable passwords — and inadvertently…
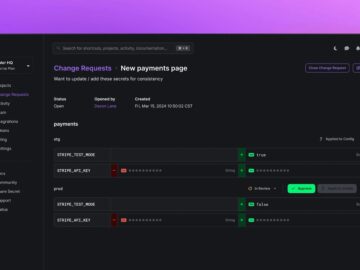
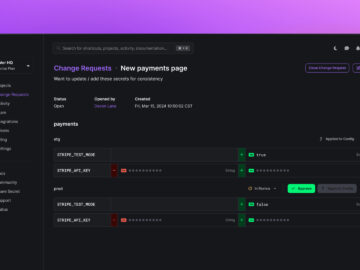
Doppler, the leading platform in secrets management, today announces the launch of Change Requests, a new feature providing engineering teams…
Doppler, the leading platform in secrets management, today announces the launch of Change Requests, a new feature providing engineering teams…
San Francisco, United States / California, October 3rd, 2024, CyberNewsWire Doppler, the leading platform in secrets management, today announces the…
Europol, in collaboration with various global law enforcement agencies, has broadened its Operation Cronos to apprehend four individuals allegedly connected…
CVE-2024-29824, an unauthenticated SQL Injection vulnerability in Ivanti Endpoint Manager (EPM) appliances, is being exploited by attackers, the Cybersecurity and…
Local authorities need more support to responsibly procure artificial intelligence (AI) systems, as existing government guidance does not provide a…
Thousands of Adobe Commerce e-stores hacked by exploiting the CosmicSting bug Pierluigi Paganini October 03, 2024 Over 4,000 unpatched Adobe…
A Linux malware named “perfctl” has been targeting Linux servers and workstations for at least three years, remaining largely undetected…
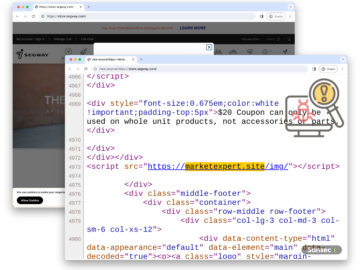
Singapore, Singapore, October 3rd, 2024, CyberNewsWire At DEF CON 32, the SquareX research team delivered a hard-hitting presentation titled Sneaky…