In late August, Intermountain Planned Parenthood of Montana suffered a cyberattack which is still under investigation. The attack has been…
Sep 05, 2024Ravie LakshmananMalware / Human Rights Unnamed government entities in the Middle East and Malaysia are the target of…
Do we all read and understand this sentence (or is it a question) in the same way? The evidence suggests…
Researchers have uncovered a novel malware dubbed KTLVdoor, linked to the Chinese-speaking threat actor Earth Lusca. This multi-platform backdoor, written…
Image: MidjourneyNorth Carolina musician Michael Smith was indicted for collecting over $10 million in royalty payments from Spotify, Amazon Music, Apple…
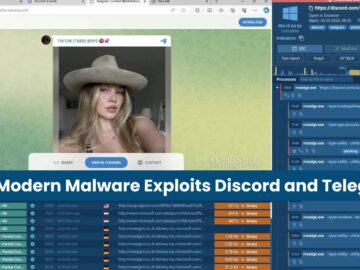
Although Discord and Telegram are some of the most popular communication channels today, they aren’t just used for chatting and…
The social network X has been largely inaccessible in Brazil since Saturday, after the country’s Supreme Court ordered all mobile…
Abusix, a network security company that offers solutions for email security and network abuse report handling, today announced the launch…
Deutsche Flugsicherung (DFS), based in Langen, Frankfurt, has recently experienced a cyber attack that had a minimal impact on its…
05 Sep Fighting AI with AI: Tools for the Twenty-First Century AI is the most effective tool in our arsenal…
In mid-August, we identified a malvertising campaign targeting Lowes employees via Google ads. Like many large corporations, Lowe’s has their…
The UK’s C-suite boasts some of the most technically savvy executives in the world, according to research by Accenture. Looking…