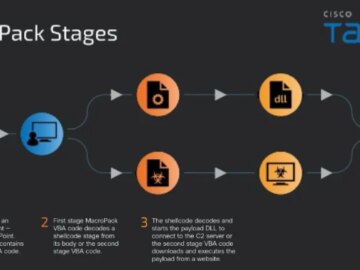
Quishing, an insidious threat to electric car owners Pierluigi Paganini September 05, 2024 Quishing is a type of phishing attack where…
Cisco Systems has issued a critical security advisory for a vulnerability in the Cisco Meraki Systems Manager (SM) Agent for…
Sep 05, 2024Ravie LakshmananCyber Threat / Malware Threat actors are likely employing a tool designated for red teaming exercises to…
The Tor Project recently revealed Tor Browser 13.5.3, marking advancements in its ongoing effort to enhance user privacy and security….
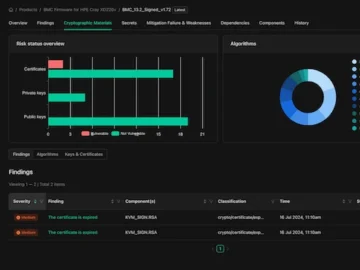
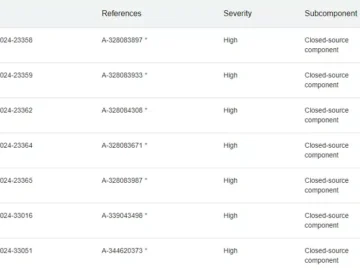
Binarly announced Binarly Transparency Platform 2.5 with several features designed to enhance software vulnerability management and improve security posture across…
The Department of Justice (DOJ) has announced the ongoing seizure of 32 internet domains tied to a Russian foreign malign…
In an updated SEC filing on September 4, 2024, American semiconductor giant Microchip Technology Incorporated disclosed new details about the…
The Tor Project has officially released Tor Browser 13.5.3, bringing many updates and improvements to enhance security and usability. This…
Sep 05, 2024Ravie LakshmananCyber Attack / Malware The Chinese-speaking threat actor known as Earth Lusca has been observed using a…
The Android Security Bulletin for September 2024 reveals critical information about vulnerabilities impacting Android devices. The bulletin highlights security issues…
Recent reports reveal a complex and contentious cyber conflict involving Iran. On one side, Iran faces allegations of orchestrating ransomware…
NBN Co will boost the speeds of its three current top-tier residential services, and introduce a new 2Gbps tier, in…