The Dutch Data Protection Authority (DPA) has imposed a hefty fine of 30.5 million euros [approximately US$33.7 million] on Clearview…
The Federal Trade Commission (FTC) requires security camera vendor Verkada to create a comprehensive information security program as part of…
Microsoft has released a new Workspaces PowerToy that helps launch sets of applications using custom desktop layouts and configurations with…
Three men have pleaded guilty to operating a website that enabled criminals to bypass banking anti-fraud checks, leading to significant…
The FBI warned today of North Korean hacking groups aggressively targeting cryptocurrency companies and their employees in sophisticated social engineering…
A significant security vulnerability has been reported in the DAP-2310, specifically affecting Hardware Revision A with Firmware version 1.16RC028. Hahna…
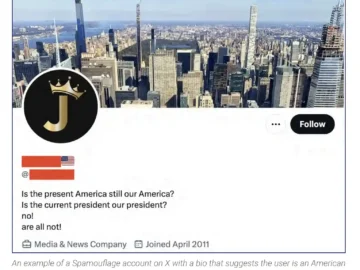
As the 2024 U.S. presidential election approaches, a Chinese state-linked influence operation known as Spamouflage has become increasingly aggressive in…
The Dutch Data Protection Authority (Dutch DPA) has imposed a fine of €30.5 million ($33.7 million) on Clearview AI for unlawful data…
Live Webcast from Monaco will Explore the Extraordinary Opportunities in an Era of Explosive Innovation and Growth Cyber A.I. Group,…
Transport for London (TfL), the city’s transport authority, is fighting through an ongoing cyberattack. TfL runs three separate units that…
Imagine flash storage that stores data in exactly the format used by applications. That’s what’s promised by key-value flash media,…
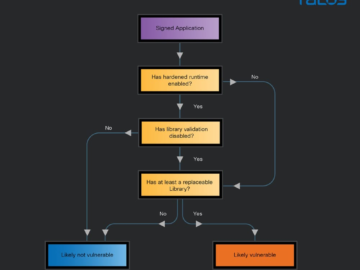
Vulnerabilities in Microsoft apps for macOS allow stealing permissions Pierluigi Paganini September 03, 2024 Vulnerabilities in Microsoft apps for macOS…