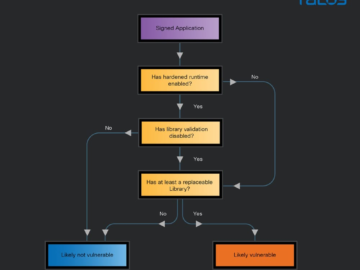
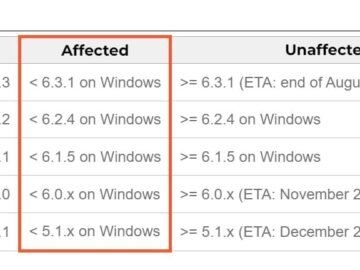
Vulnerabilities in Microsoft apps for macOS allow stealing permissions Pierluigi Paganini September 03, 2024 Vulnerabilities in Microsoft apps for macOS…
Oil and gas giant Halliburton has confirmed in a filing today to the Securities and Exchange Commission (SEC) that data…
A critical vulnerability has been identified in the Bonjour service, specifically in the mDNSResponder.exe process, which is used for network…
Miami, New York, Paris, Worldwide, September 3rd, 2024, CyberNewsWire Live Webcast from Monaco will Explore the Extraordinary Opportunities in an…
Sep 03, 2024Ravie LakshmananEndpoint Security / Malware Cybersecurity researchers have unpacked the inner workings of a new ransomware variant called…
Financial services company BBVA has received approval from the UK regulator for a takeover of Spanish rival Sabadell, which would…
The Indian Computer Emergency Response Team (CERT-IN) has issued advisories regarding critical vulnerabilities affecting several Palo Alto Networks applications. These…
U.S. oil giant Halliburton disclosed a data breach Pierluigi Paganini September 03, 2024 U.S. oil company Halliburton disclosed a data…
D-Link is warning that four remote code execution (RCE) flaws impacting all hardware and firmware versions of its DIR-846W router…
Chromium is the foundation for many popular web browsers including Google Chrome and Microsoft Edge, and this is the most…
An old but persistent email scam known as “sextortion” has a new personalized touch: The missives, which claim that malware…
Three men plead guilty to running OTP Agency, a website that enabled criminals to bypass banking security and commit fraud….