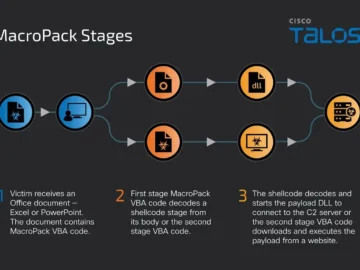
Cybercriminals may have leveraged MacroPack, a legitimate framework designed for red team exercises to distribute malicious payloads, such as the…
NBN Co has appointed Vocus chief Ellie Sweeney as its new CEO, filling the role vacated by Stephen Rue in…
VMware fixed a code execution flaw in Fusion hypervisor Pierluigi Paganini September 03, 2024 VMware released a patch to address…
What is FUD? Fear, Uncertainty, and Doubt (FUD), are central blockers to high-efficacy security programs by creating a climate of…
Managing an organization’s attack surface is a complex problem involving asset discovery, vulnerability analysis, and continuous monitoring. There are multiple…
The U.S. Federal Trade Commission (FTC) has reported a massive increase in losses to Bitcoin ATM scams, nearly ten times…
Blackwired, the leading cyber observatory for disruptive cybersecurity technologies, has announced the launch of ThirdWatch℠, a groundbreaking solution to identify…
The Dutch Data Protection Authority (DPA) has imposed a hefty fine of 30.5 million euros [approximately US$33.7 million] on Clearview…
The Federal Trade Commission (FTC) requires security camera vendor Verkada to create a comprehensive information security program as part of…
Microsoft has released a new Workspaces PowerToy that helps launch sets of applications using custom desktop layouts and configurations with…
Three men have pleaded guilty to operating a website that enabled criminals to bypass banking anti-fraud checks, leading to significant…
The FBI warned today of North Korean hacking groups aggressively targeting cryptocurrency companies and their employees in sophisticated social engineering…