An old but persistent email scam known as “sextortion” has a new personalized touch: The missives, which claim that malware…
Three men plead guilty to running OTP Agency, a website that enabled criminals to bypass banking security and commit fraud….
A new ransomware, identified as Cicada 3301, is currently making waves on the internet, targeting both Windows and Linux systems….
03 Sep Hacking Stereotypes: Women In Hollywood Films Posted at 08:57h in Blogs by Di Freeze This week in cybersecurity…
The City of Columbus, Ohio is suing a security researcher for sharing stolen data. All the complaint will accomplish, we…
Sep 03, 2024Ravie LakshmananRansomware / Malware A hacktivist group known as Head Mare has been linked to cyber attacks that…
Sweden’s legal profession has opened a national discussion to examine how evolving disrupter technologies like artificial intelligence (AI) will impact…
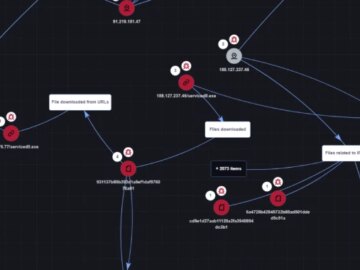
Hackers often target VPNs for several illicit purposes like injecting malicious code, stealing sensitive data, and many more. Besides this,…
Access management is an essential aspect of an organization’s security infrastructure, designed to protect and manage access to information and…
“Having the ability to reach out to friends or family allows our sailors the opportunity to decompress for a few…
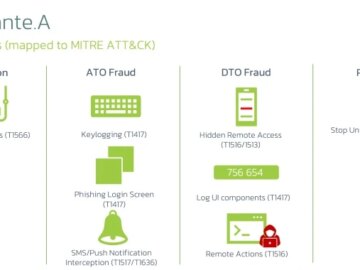
Mobile users in Brazil are the target of a new malware campaign that delivers a new Android banking trojan named…
Flash drive prices fell steadily over the first three quarters of 2024 to an average of $0.085 per gigabyte (GB)…