Critical RCE vulnerability found in OpenPLC Pierluigi Paganini September 26, 2024 Cisco’s Talos reported critical and high-severity flaws in OpenPLC…
The Tor Project and Tails OS are merging operations to better collaborate for a free internet by protecting users from…
In today’s digital age, it’s become increasingly apparent that many individuals share details of their lives online, whether intentionally or…
Azure Automation is a service that automates processes across various cloud platforms, making it easier to manage complicated hybrid setups. …
Multiple rail stations across the UK have recently fallen victim to a cyberattack that has severely disrupted public Wi-Fi connectivity….
Sep 26, 2024Ravie LakshmananAutomotive Industry / Technology Cybersecurity researchers have disclosed a set of now patched vulnerabilities in Kia vehicles…
Addressing Inconsistencies in Vulnerability Scanning One of the primary challenges of vulnerability scanning is maintaining consistent results. Inconsistencies can lead…
The U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) has sanctioned Cryptex and PM2BTC, two cryptocurrency exchanges that laundered…
Hackers are increasingly weaponizing PDF files to deliver malware and carry out cyberattacks. They exploit the all-presence and trustworthiness of…
The UK town of Blyth in Northumberland is set to become home to Europe’s biggest datacentre devoted to housing artificial…
In a move to enhance cybersecurity, the Cybersecurity and Infrastructure Security Agency (CISA), in collaboration with several international cybersecurity agencies,…
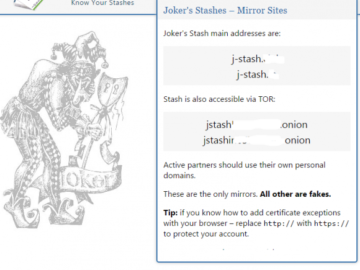
The United States today unveiled sanctions and indictments against the alleged proprietor of Joker’s Stash, a now-defunct cybercrime store that…