Microsoft discovered a North Korean threat actor exploiting a zero-day vulnerability in the Chromium browser, identified as CVE-2024-7971. This vulnerability,…
Google to Revise One-Time Password (OTP) Process Google is set to introduce new rules for handling One-Time Passwords (OTPs) on…
Sep 02, 2024The Hacker NewsCybercrime / CISO Insights The FBI and CISA Issue Joint Advisory on New Threats and How…
After a sizeable uptick in the immediate post-pandemic world of work, questions are being raised over whether the software-defined wide…
German Air Traffic Control Deutsche Flugsicherung (DFS) has notified that it has fallen victim to a cyberattack. The Deutsche Flugsicherung…
Australian consumers want to feel secure with familiar brands while paying online and are less likely to use digital currencies…
A new variant of Cicada ransomware targets VMware ESXi systems Pierluigi Paganini September 02, 2024 A new ransomware-as-a-service (RaaS) operation…
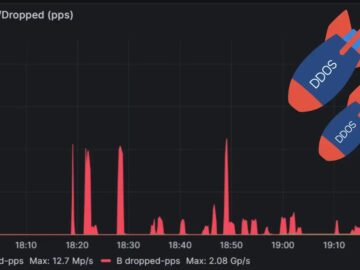
Global Secure Layer (GSL) successfully mitigated the most considerable packet rate of the Distributed Denial of Service (DDoS) attack ever…
Traveling can be an exciting and enriching experience, but it also exposes you to various cybersecurity risks. Whether you’re exploring…
Global freight forwarder JAS Worldwide has provided an update following last week’s cyberattack, announcing that its central operations are now…
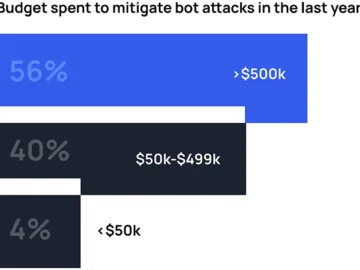
98% of organizations attacked by bots in the past year lost revenue as a result, according to Kasada. Web scraping…
And when the equipment in question is out of warranty or many years old, The chances of having spare parts…