NBN Co is working to a new five-year security strategy that will help the network operator comply with the government’s…
TPG Telecom is to axe 19 enterprise, government and wholesale products this year, with eight shuttered in the past six…
Image: Midjourney A new ransomware-as-a-service (RaaS) operation named Cicada3301 has already listed 19 victims on its extortion portal, as it…
The popular Docker-OSX project has been removed from Docker Hub after Apple filed a DMCA (Digital Millennium Copyright Act) takedown…
Welcome to this week’s edition of our Weekly Cybersecurity Newsletter, your go-to source for the latest developments and insights in the…
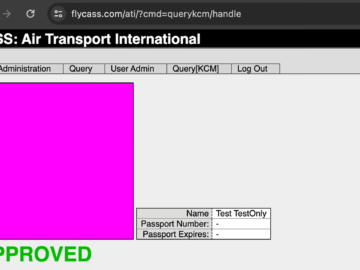
An air transport security system flaw allowed to bypass airport security screenings Pierluigi Paganini September 01, 2024 A vulnerability in…
GitHub is being abused to distribute the Lumma Stealer information-stealing malware as fake fixes posted in project comments. The campaign…
Fraud prevention today is like a game of whack-a-mole. When one fraudster or attack method is stamped out, another arises…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: SonicWall patches critical flaw affecting…
North Korea-linked APT Citrine Sleet exploit Chrome zero-day to deliver FudModule rootkit Pierluigi Paganini August 31, 2024 North Korea-linked APT…
Aug 31, 2024Ravie LakshmananRootkit / Threat Intelligence A recently patched security flaw in Google Chrome and other Chromium web browsers…
31 Aug ‘Time-Travelling’ Software Could Bankrupt Hackers Posted at 09:46h in Blogs by Di Freeze This week in cybersecurity from…