Sep 03, 2024Ravie LakshmananInsider Threat / Network Security A 57-year-old man from the U.S. state of Missouri has been arrested…
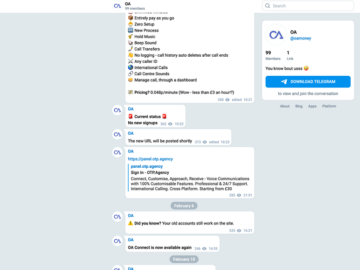
Three men have pleaded guilty to running OTP.Agency, an online platform that provided social engineering help to obtain one-time passcodes from…
Pioneering Pentest as a Service (PtaaS) for Enhanced Offensive Security At BlackHat, we had the opportunity to speak with Jason…
Revolutionizing Network Security Automation I recently spoke with Rekha Shenoy, CEO of BackBox during the BlackHat conference, and her insights…
Tracelo, a smartphone geolocation tracker service, was breached on September 1, 2024, exposing data from both its customers and the…
Image: Transport for LondonTransport for London (TfL), the city’s transport authority, is investigating an ongoing cyberattack that has yet to…
Revolutionizing Identity Security with AI-Driven Solutions At BlackHat 2024, we had the pleasure of discussing the future of identity security…
Three men in the United Kingdom have pleaded guilty to operating otp[.]agency, a once popular online service that helped attackers…
Revolutionizing Cybersecurity with Automated Security Validation In a conversation with Jay Mar-Tang, Field CISO at Pentera, it became clear that…
Remote work offers benefits like reduced costs and wider recruitment but also increases cybersecurity risks. To protect your business, provide…
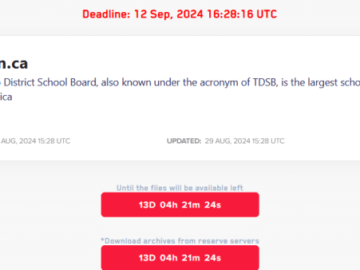
On the same day as LockBit ransomware gang claimed attack on the largest district school board in Canada, the Board…
The Federal Trade Commission (FTC) proposes a $2.95 million penalty on security camera vendor Verkada for multiple security failures that enabled…