A new variant of Cicada ransomware targets VMware ESXi systems Pierluigi Paganini September 02, 2024 A new ransomware-as-a-service (RaaS) operation…
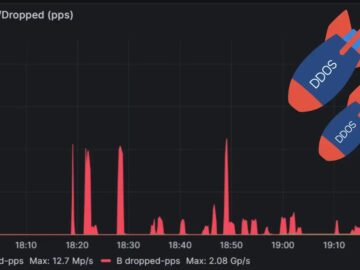
Global Secure Layer (GSL) successfully mitigated the most considerable packet rate of the Distributed Denial of Service (DDoS) attack ever…
Traveling can be an exciting and enriching experience, but it also exposes you to various cybersecurity risks. Whether you’re exploring…
Global freight forwarder JAS Worldwide has provided an update following last week’s cyberattack, announcing that its central operations are now…
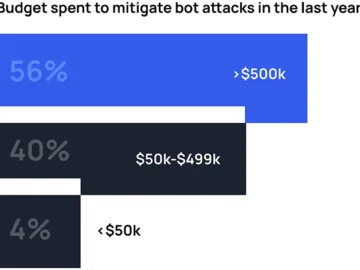
98% of organizations attacked by bots in the past year lost revenue as a result, according to Kasada. Web scraping…
And when the equipment in question is out of warranty or many years old, The chances of having spare parts…
Damn Vulnerable UEFI (DVUEFI) is an open-source exploitation toolkit and learning platform for unveiling and fixing UEFI firmware vulnerabilities. Simulate…
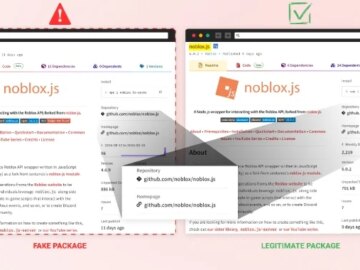
Sep 02, 2024Ravie LakshmananSoftware Security / Malware Roblox developers are the target of a persistent campaign that seeks to compromise…
Bendigo and Adelaide Bank has tapped the chief executive of its neobank Up to hold the additional role of chief…
During the second quarter, new ransomware groups, including PLAY, Medusa, RansomHub, INC Ransom, BlackSuit, and some additional lesser-known factions, led…
A new ransomware group, Cicada3301, has emerged, targeting Windows and Linux/ESXi hosts with sophisticated encryption techniques. First observed in June…
Here’s a look at the most interesting products from the past month, featuring releases from: Adaptive Shield, AppOmni, ArmorCode, Bitwarden,…