Google will redact your credit card details, passwords and other sensitive information in Chrome when you’re sharing or recording your…
From 2018: DeepMasterPrints: deceive fingerprint recognition systems with MasterPrints generated with GANs Pierluigi Paganini August 18, 2024 Boffins demonstrated the…
Navigating the Cybersecurity Landscape: Achieving Impactful Wins Through Data, Collaboration, and Continuous Improvement Do not think of advocating for critical…
The “Weekly Cyber Security News Letter – Data Breaches, Vulnerability, Cyber Attack & More” provides a comprehensive overview of the…
Security Affairs newsletter Round 485 by Pierluigi Paganini – INTERNATIONAL EDITION Pierluigi Paganini August 18, 2024 A new round of…
Large-scale extortion campaign targets publicly accessible environment variable files (.env) Pierluigi Paganini August 18, 2024 A large-scale extortion campaign compromised…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Unpatched MS Office flaw may…
OpenAI dismantled an Iranian influence operation targeting the U.S. presidential election Pierluigi Paganini August 17, 2024 OpenAI announced it had…
One-time passwords (OTPs) have become a cornerstone of modern cybersecurity, offering an additional layer of protection for online accounts. However,…
National Public Data confirms a data breach Pierluigi Paganini August 17, 2024 Background check service National Public Data confirms a…
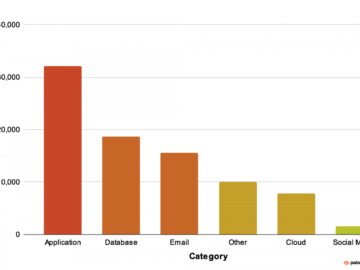
Security Information Event Management (SIEM) technology has come far over the past two decades. SIEM is a critical part of…
A clever disinformation campaign engages several Microsoft Azure and OVH cloud subdomains as well as Google search to promote malware and…