A new data extortion group tracked as Mad Liberator is targeting AnyDesk users and runs a fake Microsoft Windows update…
The 2024 US presidential election is entering its final stretch, which means state-backed hackers are slipping out of the shadows…
17 Aug ‘Sinkclose’ vulnerability affects hundreds of millions of AMD Chips Posted at 09:52h in Blogs by Di Freeze This…
The resurgence of banking trojans has become a major cybersecurity concern for financial institutions and their customers. These malicious backdoor…
A critical 7-year-old security flaw in a pre-installed app on millions of Google Pixel devices has been exposed. The vulnerability…
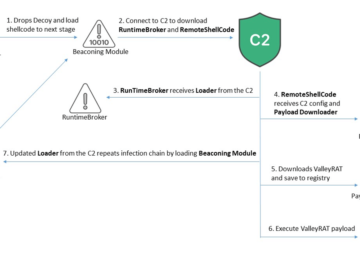
ValleyRAT malware is targeting Chinese-speaking users Pierluigi Paganini August 17, 2024 FortiGuard Labs researchers uncovered an ongoing ValleyRAT malware campaign…
OpenAI on Friday said it banned a set of accounts linked to what it said was an Iranian covert influence…
Security researchers at Avast have uncovered evidence that the notorious North Korean hacker group Lazarus exploited a previously unknown zero-day…
The Committee on Foreign Investment in the United States (CFIUS), a U.S. government agency responsible for reviewing foreign investments in…
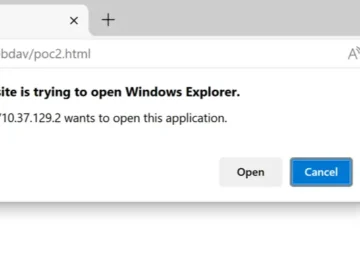
Security experts recently uncovered a vulnerability, CVE-2024-38213, that allows threat actors to bypass Windows’ Mark-of-the-Web (MotW) protections through copy-and-paste operations….
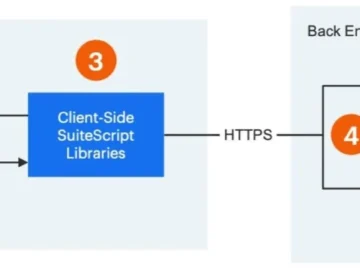
Oracle’s NetSuite, a popular Enterprise Resource Planning (ERP) platform, has a feature that allows businesses to deploy an external-facing store…
Microsoft has shared a workaround for a known issue affecting Microsoft 365 customers and causing classic Outlook to crash after…