Russian national sentenced to 40 months for selling stolen data on the dark web Pierluigi Paganini August 16, 2024 A…
As we move through 2024, the Wallarm Research Team continues to monitor the evolving API vulnerability and threat landscape. Our…
IT admins usually know what to watch out for when end users are creating weak, easy-to-guess passwords. However, a common…
Cary, United States / North Carolina, August 16th, 2024, CyberNewsWire INE Security Experts Explain How To Integrate Proper Cybersecurity Training …
Background check service National Public Data confirms that hackers breached its systems after threat actors leaked a stolen database with…
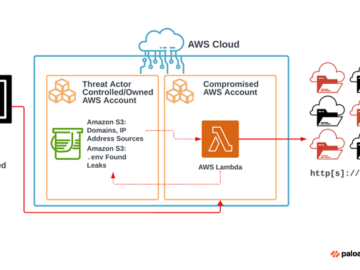
Aug 16, 2024Ravie LakshmananCloud Security / Application Security A large-scale extortion campaign has compromised various organizations by taking advantage of…
Image: MidjourneyCISA warned on Thursday that attackers are exploiting a recently patched critical vulnerability in SolarWinds’ Web Help Desk solution…
With the growing convenience of smartphones, many users have become accustomed to storing sensitive information such as credit and debit…
Thousands of organisations using NetSuite SuiteCommerce are unknowingly exposing their most sensitive data as a result of misconfigured access controls…
Aug 16, 2024Ravie LakshmananDark Web / Data Breach A 27-year-old Russian national has been sentenced to over three years in…
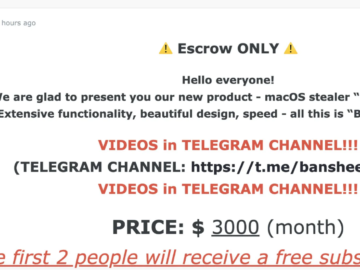
Banshee Stealer, a new macOS malware with a monthly subscription price of $3,000 Pierluigi Paganini August 16, 2024 Russian cybercriminals…
Once viewed with caution, ethical hackers are now regarded as an essential asset for many cybersecurity teams around the globe….