In a significant move to fortify the security posture of its cloud platform, Microsoft is implementing mandatory Multi-Factor Authentication (MFA)…
Microsoft has released Windows 11 Build 27686 with some hidden HDR-related changes. As noticed by Phantom on X, one of the hidden…
Discover how GitHub Actions artifacts leak sensitive authentication tokens, exposing popular open-source projects to security risks. Learn about the ArtiPACKED…
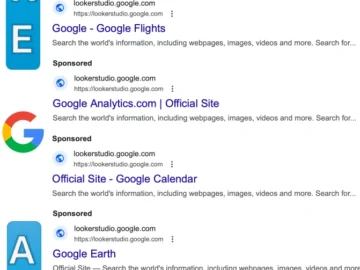
Google Search ads that target users looking for Google’s own services lead them to spoofed sites and Microsoft and Apple…
A cyberattack has recently rocked Greater Manchester, compromising the security of several local councils and leaving thousands of residents vulnerable…
An Android package, “Showcase.apk,” preinstalled on a significant portion of Pixel devices since 2017, possesses extensive system permissions enabling remote…
I recently spent six days in Las Vegas attending DEF CON, BsidesLV, and Black Hat USA 2024, where I had…
Aug 16, 2024Ravie LakshmananMalware / Browser Security Cybersecurity researchers have uncovered new stealer malware that’s designed to specifically target Apple…
Demand is fast-outstripping supply in terms of datacentre capacity across Europe, with quarterly market data from real estate consultancy CBRE…
As the United States gears up for what is anticipated to be a highly active US general election 2024 season,…
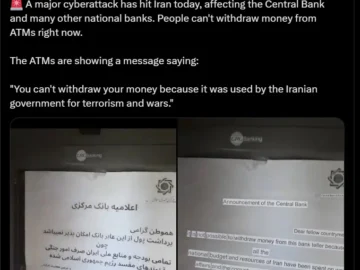
The Central Bank of Iran (CBI) and several other banks in the country fell victim to a significant cyberattack on…
Millions of Pixel devices can be hacked due to a pre-installed vulnerable app Pierluigi Paganini August 16, 2024 Many Google…