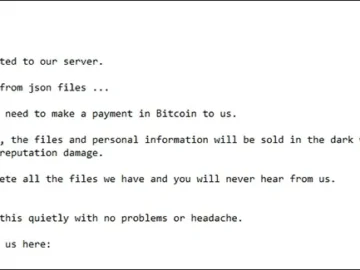
The Rhysida Ransomware gang, a notorious group known for their file-encrypting malware, has announced that they will be selling data…
Aug 15, 2024Ravie LakshmananEnterprise Security / Vulnerability SolarWinds has released patches to address a critical security vulnerability in its Web…
In 2006, Amazon Web Services (AWS), the first public cloud provider, offered publicly available services such as Elastic Computer Cloud…
NIST, an agency in the federal government of the United States (US), has finished its first draft of cryptographic algorithms…
Cybersecurity researchers have uncovered a sophisticated malspam campaign targeting unsuspecting users through email and phone calls. Attackers are leveraging popular…
In the final week of the Tour de France, cyclists endure grueling conditions of hills, heat, and pain over 21…
Cybercriminals are breaking into organizations’ cloud storage containers, exfiltrating their sensitive data and, in several cases, have been paid off…
The number of girls choosing to take computing at A-level in 2024 increased by almost 800 students, pushing the total…
Microsoft has shared a temporary fix for a known issue that causes Microsoft 365 apps like Outlook, Word, and OneNote…
Researchers have uncovered a new and previously undocumented malware platform named “Cyclops.” Written in the Go programming language, Cyclops has…
A ransomware group known as RansomHub has been found deploying a new tool designed to disable endpoint detection and response…
Securing the software supply chain has become a top priority due to high-profile breaches and increasing regulatory scrutiny. International agencies…