During the Election Center 39th Annual National Conference held in Detroit on September 9, 2024, Jen Easterly, the Director of…
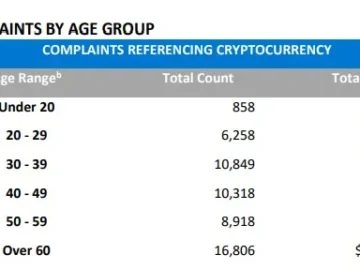
The FBI’s Cryptocurrency Fraud Report for 2023, highlights a sharp rise in cyber-enabled financial crimes involving cryptocurrency. In 2023 alone,…
A new variant of the ongoing sextortion email scams is now targeting spouses, saying that their husband or wife is…
Tropic Trooper (aka KeyBoy, Pirate Panda, and APT23) is a sophisticated cyberespionage APT group, and it has been active since…
Crashes due to faulty updates are nothing new; in fact, one reason IT teams often delay updates is their unreliability…
From zero-day exploits to polymorphic malware, today’s organizations must protect themselves against increasingly sophisticated cyber threats. But while these types of complex attack vectors…
Recent research indicates that the Predator spyware, once thought to be inactive due to US sanctions, has resurfaced with enhanced…
IT leaders plan to spend more in 2025 compared to 2024, the Budget planning guides from analyst Forrester has reported….
New attacks attributed to China-based cyber espionage group Mustang Panda show that the threat actor switched to new strategies and…
WhatsApp’s “View Once” feature, designed to enhance privacy by allowing users to send photos and videos that disappear after being…
Cybercriminals in Latin America have increased their use of phishing scams targeting business transactions and judicial-related matters. By leveraging trust…
Finding and acquiring the right data to build an enterprise dataset is perhaps the most critical task facing organisations that…