A significant security vulnerability has been reported in the DAP-2310, specifically affecting Hardware Revision A with Firmware version 1.16RC028. Hahna…
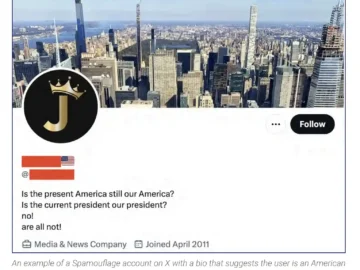
As the 2024 U.S. presidential election approaches, a Chinese state-linked influence operation known as Spamouflage has become increasingly aggressive in…
The Dutch Data Protection Authority (Dutch DPA) has imposed a fine of €30.5 million ($33.7 million) on Clearview AI for unlawful data…
Live Webcast from Monaco will Explore the Extraordinary Opportunities in an Era of Explosive Innovation and Growth Cyber A.I. Group,…
Transport for London (TfL), the city’s transport authority, is fighting through an ongoing cyberattack. TfL runs three separate units that…
Imagine flash storage that stores data in exactly the format used by applications. That’s what’s promised by key-value flash media,…
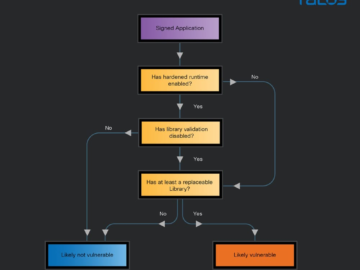
Vulnerabilities in Microsoft apps for macOS allow stealing permissions Pierluigi Paganini September 03, 2024 Vulnerabilities in Microsoft apps for macOS…
Oil and gas giant Halliburton has confirmed in a filing today to the Securities and Exchange Commission (SEC) that data…
A critical vulnerability has been identified in the Bonjour service, specifically in the mDNSResponder.exe process, which is used for network…
Miami, New York, Paris, Worldwide, September 3rd, 2024, CyberNewsWire Live Webcast from Monaco will Explore the Extraordinary Opportunities in an…
Sep 03, 2024Ravie LakshmananEndpoint Security / Malware Cybersecurity researchers have unpacked the inner workings of a new ransomware variant called…
Financial services company BBVA has received approval from the UK regulator for a takeover of Spanish rival Sabadell, which would…