Commonwealth Bank has opened yet another avenue in its progression of AI, funding a new centre and research partnership with…
In this Help Net Security interview, Henrik Plate, CISSP, security researcher, Endor Labs, discusses the complexities AppSec teams face in…
Google has announced the release of Chrome 129, which is now available on the stable channel for Windows, Mac, and…
Application Security Engineer CHANEL | France | On-site – View job details As an Application Security Engineer, you will perform…
The Australian Federal Police gained access to an encrypted communications platform called Ghost by tampering with regular software updates pushed…
Organizations are combating excessive remote access demands with an equally excessive number of tools that provide varying degrees of security,…
Data centres have evolved from the backrooms and basements of IT departments to become the critical infrastructure that drives business…
VMware has disclosed two critical security vulnerabilities affecting its vCenter Server and Cloud Foundation products that could allow attackers to…
Remote attack on pagers used by Hezbollah caused 9 deaths and thousands of injuries Pierluigi Paganini September 17, 2024 Remote…
Facebook owner Meta said it was banning RT, Rossiya Segodnya and other Russian state media networks from its platforms, claiming…
Temu denies it was hacked or suffered a data breach after a threat actor claimed to be selling a stolen database…
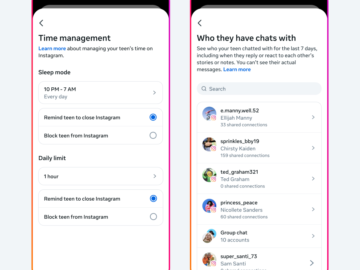
Instagram’s latest move to protect its younger audience takes shape with the introduction of “Teen Accounts.” Starting today, teens under…