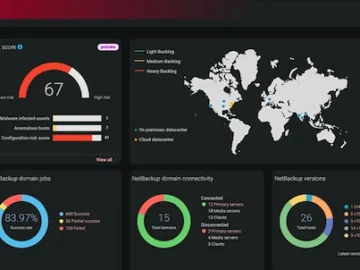
Veritas Technologies unveiled new AI-driven capabilities to further expand the strength and functionality of the Veritas cyber resilience portfolio. The…
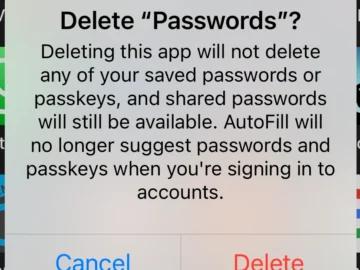
On September 16, 2024, Apple released iOS 18. Besides a lot of exciting new features, iOS 18 comes with some…
Sep 17, 2024Ravie LakshmananSpyware / Privacy The U.S. Department of Treasury has imposed fresh sanctions against five executives and one…
On 29 July 2024, in a story that has now become seared into the British psyche, Axel Rudakubana murdered three…
Apple has officially released iOS 18, which is the latest software update for iPhones and iPads. While the software introduces…
As buzz and excitement continues to build around the upcoming 2024 Summer Olympics, it is important to be aware of the…
Apple has launched iOS 18, the latest significant iteration of the operating system powering its iPhones. Along with many new…
Sep 17, 2024Ravie LakshmananBrowser Security / Quantum Computing Google has announced that it will be switching from KYBER to ML-KEM…
Payment card data theft remains a huge problem and still accounts for almost a fifth (19%) of breaches, with that…
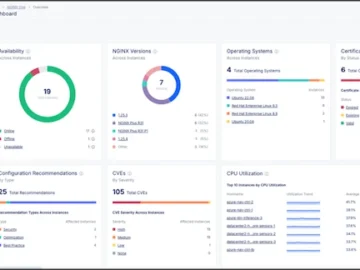
F5 launched F5 NGINX One, combining advanced load balancing, web and application server capabilities, API gateway functionalities, and security features…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent warning regarding two critical vulnerabilities affecting Microsoft Windows MSHTML…
Sep 17, 2024The Hacker NewsGenAI Security / SaaS Security Since launching ChatGPT in 2022, OpenAI has defied expectations with a…