Lessons from CrowdStrike on Safeguarding Your Data with Compliance, Continuity and Disaster Recovery Strategies Where were you when the CrowdStrike…
Service accounts are non-human identities used to automate machine-to-machine interactions. They support critical functions – such as running scripts, services,…
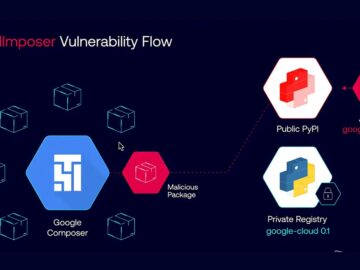
Security researchers revealed this week that a critical remote code execution (RCE) vulnerability in Google Cloud Platform (GCP) could have…
You wouldn’t brush your teeth once a year — it just wouldn’t be frequent enough to maintain proper care and…
In this Help Net Security interview, Robert Ramsey, CEO at Rain Technology, discusses the growing threat of visual hacking, how…
Due to its wide acceptance, SAP has become a favorite target for hackers. With the ubiquity of SAP Enterprise Resource…
The global cybersecurity workforce gap reached a new high with an estimated 4.8 million professionals needed to effectively secure organizations,…
Mining has always been a high-demand sector. It’s becoming increasingly challenging, as a result of complex and stringent third-party approvals,…
Government was the second-most breached sector in Australia during the first six months of 2024, reporting 63 incidents in total….
The Biden Administration has awarded Intel up to US$3 billion ($4.44 billion) from the CHIPS and Science Act to develop…
The U.S. Treasury Department today sanctioned five individuals and one entity associated with the Intellexa Consortium for their role in…
Vista Equity Partners and Blackstone are in advanced talks to acquire Smartsheet, in a deal that could value the collaboration…