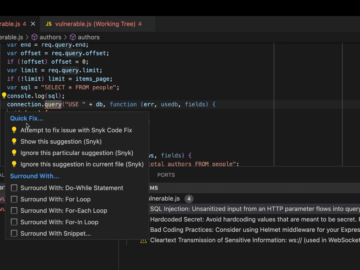
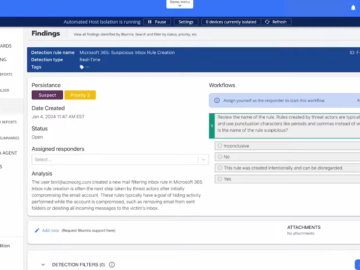
It’s time to give your development process a boost. We’ve all been there staring at a security issue, trying to…
Researchers uncovered a sophisticated phishing campaign that exploits a .NET-based Snake Keylogger variant. This attack leverages weaponized Excel documents to…
I was thrilled to catch up with Blumira during Black Hat USA 2024. When it comes to resource-constrained businesses, traditional…
Aug 30, 2024Ravie LakshmananMalware / Network Security Cybersecurity researchers have disclosed a new campaign that potentially targets users in the…
The Communication Challenge in Cybersecurity The vulnerability management process involves various stakeholders, each with their own expertise and communication styles….
The City of Columbus, Ohio, has filed a lawsuit against security researcher David Leroy Ross, aka Connor Goodwolf, accusing him…
In the ever-evolving landscape of cybersecurity, malware obfuscation techniques are advancing rapidly. As security measures improve, so do malicious actors’…
Cary, North Carolina, August 30th, 2024, CyberNewsWire: INE Security is pleased to announce that it has been recognized as a…
Cybersecurity researchers have uncovered a novel malware campaign that leverages Google Sheets as a command-and-control (C2) mechanism. The activity, detected…
Recent security findings reveal that Progress Software’s WhatsUp Gold, a prominent enterprise network monitoring and management solution, harbors significant vulnerabilities…
Cary, North Carolina, August 30th, 2024, CyberNewsWire: INE Security is pleased to announce that it has been recognized as a…
Researchers from Proofpoint have uncovered a sophisticated cyberattack campaign leveraging Google Sheets as a command and control (C2) platform. Dubbed…