Researchers from Technische Universität Clausthal in Germany and CUBE Global in Australia have explored the potential of ChatGPT, a large…
The Russian ransomware group Key Group, active since early 2023, is targeting organizations globally, as their modus operandi involves encrypting…
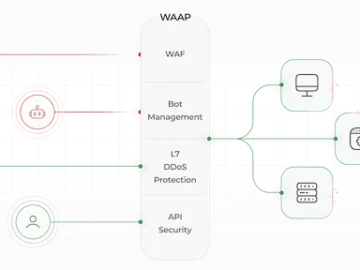
Gcore launched Gcore WAAP, its end-to-end web application and API protection solution. Leveraging AI capabilities, Gcore WAAP integrates four products…
Number three in the hard drive maker’s league, Toshiba, has announced products of 24TB and 28TB. These are the 24TB…
U.S. CISA adds Microsoft Windows MSHTML Platform and Progress WhatsUp Gold bugs to its Known Exploited Vulnerabilities catalog Pierluigi Paganini September…
Honeypots, decoy systems, detect and analyze malicious activity by coming in various forms and can be deployed on cloud platforms…
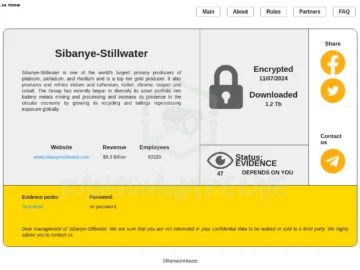
Sibanye-Stillwater, a mining company and the operator of the only platinum and palladium mines in the U.S., has confirmed a…
Qilin ransomware attack on Synnovis impacted over 900,000 patients Pierluigi Paganini September 17, 2024 The personal information of a million…
North Korean hackers have been identified as targeting LinkedIn users to deliver sophisticated malware known as RustDoor. This cyber threat…
Thank you for joining! Access your Pro+ Content below. 17 September 2024 The pillars of AI strategy Share this item…
Taking Control Online: Ensuring Awareness of Data Usage and Consent Pierluigi Paganini September 17, 2024 Why do consumers refuse to…
Ivanti Endpoint Manager, a widely used IT management software, has discovered a critical security vulnerability. CVE-2024-29847 vulnerability allows for remote…