As the new academic year unfolds, educational institutions are facing an increasingly alarming threat: ransomware attacks. According to a recent…
Sep 13, 2024Ravie LakshmananVirtual Reality / Vulnerability Details have emerged about a now-patched security flaw impacting Apple’s Vision Pro mixed…
Kawasaki Motors Europe has announced that it’s recovering from a cyberattack that disrupted service disruptions as the RansomHub ransomware gang…
In cybersecurity, brute force attacks are a well-known and persistent threat. Despite being one of the oldest methods hackers use,…
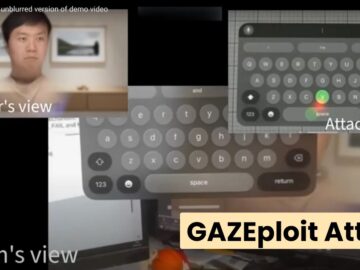
A novel security vulnerability dubbed “GAZEploit” has been discovered that could allow hackers to capture keystrokes from Apple Vision Pro’s…
Sep 13, 2024Ravie LakshmananSoftware Security / Threat Intelligence Malicious actors are likely leveraging publicly available proof-of-concept (PoC) exploits for recently…
Lehigh Valley Health Network hospital network has agreed to a $65 million settlement after data breach Pierluigi Paganini September 13,…
An Android TV Box is a small device that connects to your TV and allows you to access a wide…
Kali Linux 2024.3, the most recent iteration of Offensive Security’s highly regarded Debian-based distribution designed for ethical hacking and penetration…
Sep 13, 2024Ravie LakshmananCyber Attack / Crime British authorities on Thursday announced the arrest of a 17-year-old male in connection…
Recently, the CEO of the world’s biggest advertising group, Mark Read, was the target of a deepfake scam using an AI-based voice…
13 Sep Mastercard Goes Deeper Into Cybersecurity With $2.65B Acquisition Of Recorded Future Posted at 09:09h in Blogs by Di…