In a recent interview with The Cyber Express on the show Security Pill, Manish Chachada, Co-Founder and COO of Cyble,…
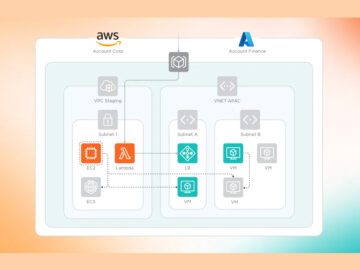
Pioneering Zero Trust Segmentation for Comprehensive Cybersecurity by Samridhi Agarwal, Master’s Student, CMU In today’s rapidly evolving cybersecurity landscape, organizations…
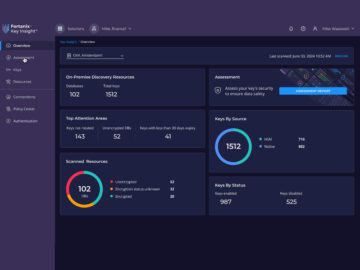
Unveiling Secure Data Practices in a World of AI Risks by Samridhi Agarwal, Master’s Student, CMU In an era where…
A Comprehensive Guide As with many other fields in technology, cybersecurity is in a constant state of evolution. One often…
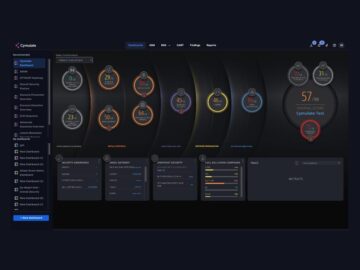
AI Copilot: Revolutionizing Threat Exposure Validation by Samridhi Agarwal, Master’s Student, CMU During BlackHat, Cymulate, a leader in security and…
Despite the vulnerabilities of proximity technology, many organizations have yet to take steps to transition to more secure credentialing systems….
GitLab fixed a critical flaw in GitLab CE and GitLab EE Pierluigi Paganini September 14, 2024 GitLab addressed multiple vulnerabilities…
Sep 14, 2024Ravie LakshmananEnterprise Security / Threat Intelligence Ivanti has revealed that a newly patched security flaw in its Cloud…
Kawasaki Motors Europe (KME) has officially confirmed it was the target of a cyberattack in early September, causing temporary disruptions…
The Port of Seattle has confirmed that the Rhysida ransomware gang orchestrated the cyberattack that disrupted its systems and operations…
Image: MidjourneyPort of Seattle, the United States government agency overseeing Seattle’s seaport and airport, confirmed on Friday that the Rhysida…
Transport for London (TfL) says that all staff (roughly 30,000 employees) must attend in-person appointments to verify their identities and…