Ivanti confirmed on Friday that a high-severity vulnerability in its Cloud Services Appliance (CSA) solution is now actively exploited in…
Car manufacturer Ford Motor Company has filed a patent application for an in-vehicle advertisement presentation system based on information derived…
Allison’s commitment to neo-fascism and white supremacy appears to have run deep—“I won’t quit til I’m dead. my only goal…
A new Android malware called Trojan Ajina.Banker is targeting Central Asia – Discover how this malicious malware disguises itself as…
As the new academic year unfolds, educational institutions are facing an increasingly alarming threat: ransomware attacks. According to a recent…
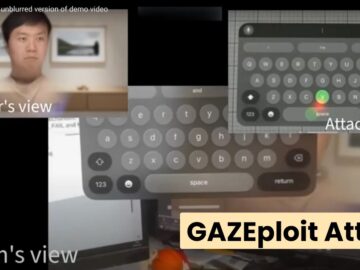
Sep 13, 2024Ravie LakshmananVirtual Reality / Vulnerability Details have emerged about a now-patched security flaw impacting Apple’s Vision Pro mixed…
Kawasaki Motors Europe has announced that it’s recovering from a cyberattack that disrupted service disruptions as the RansomHub ransomware gang…
In cybersecurity, brute force attacks are a well-known and persistent threat. Despite being one of the oldest methods hackers use,…
A novel security vulnerability dubbed “GAZEploit” has been discovered that could allow hackers to capture keystrokes from Apple Vision Pro’s…
Sep 13, 2024Ravie LakshmananSoftware Security / Threat Intelligence Malicious actors are likely leveraging publicly available proof-of-concept (PoC) exploits for recently…
Lehigh Valley Health Network hospital network has agreed to a $65 million settlement after data breach Pierluigi Paganini September 13,…
An Android TV Box is a small device that connects to your TV and allows you to access a wide…