Palo Alto Networks has disclosed a high-severity command injection vulnerability in its PAN-OS software that could allow authenticated administrators to…
A critical vulnerability in the Apache OFBiz framework has been actively exploited by hackers. The flaw designated CVE-2024-45195, allows for…
UK data centers are now critical assets, at power with electricity grids and water supply systems. In a landmark move,…
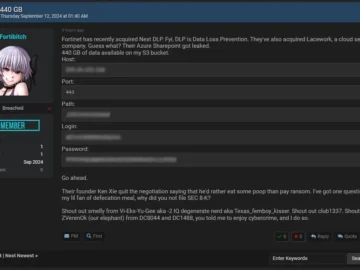
Cybersecurity giant Fortinet, known for its firewalls and network security solutions, has confirmed a cybersecurity incident affecting its systems. The…
SolarWinds, a leading provider of IT management software, has recently disclosed critical vulnerabilities in its Access Rights Manager (ARM) platform….
The evolution of network security mirrors the broader technological landscape: a journey from simplicity to complexity, from reactive to proactive…
The discussion, featuring Beenu Arora, CEO and Co-Founder of Cyble, examined the potential impact of this acquisition on businesses and…
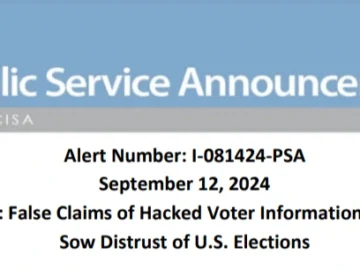
The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) have highlighted a growing concern about…
Docker has addressed critical vulnerabilities in Docker Desktop that could allow attackers to execute remote code. These vulnerabilities, identified as…
Here’s a look at the most interesting products from the past week, featuring releases from Druva, Huntress, Ketch, LOKKER, Tenable,…
Sep 13, 2024Ravie LakshmananEnterprise Security / Vulnerability Cybersecurity researchers have uncovered a new malware campaign targeting Linux environments to conduct…
Mastercard, a leading financial institution renowned for its payment solutions, has significantly strengthened its position in the field of cybersecurity…