Aug 30, 2024The Hacker NewsICS Security / OT Security A comprehensive guide authored by Dean Parsons emphasizes the growing need…
The arrest of Pavel Durov, the founder and CEO of Telegram, on August 24, 2024, has ignited an international uproar…
Mandiant has discovered one of the unusual Iranian counterintelligence activities that focuses on prospective agents of foreign intelligence services, especially…
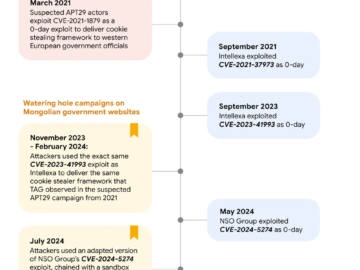
Hackers have been exploiting vulnerabilities in iOS and Google Chrome to target government websites, particularly in Mongolia. Google’s Threat Analysis…
Palo Alto Networks is currently being misused as a cover for malware distribution. Although the California-based cybersecurity company is not…
Aug 30, 2024Ravie LakshmananCryptocurrency / Malware Threat actors with ties to North Korea have been observed publishing a set of…
The Cybersecurity and Infrastructure Security Agency (CISA) announced the launch of its new CISA Services Portal, which includes an updated…
The Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), Multi-State Information Sharing and Analysis Center (MS-ISAC), and…
Russia-linked APT29 reused iOS and Chrome exploits previously developed by NSO Group and Intellexa Pierluigi Paganini August 30, 2024 Russia-linked…
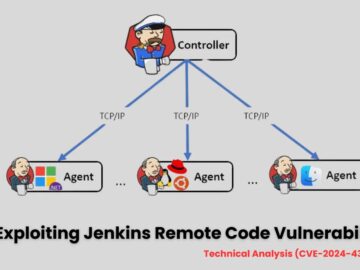
A critical vulnerability has been identified in Jenkins, a widely used automation server. If exploited further, this vulnerability allows attackers…
In recent years, ransomware attacks have evolved from mere cyber-criminal activities into sophisticated tools of geopolitical maneuvering. As the digital…
Access Control Lists (ACLs) are fundamental to network security and management. They are critical in determining who or what can…