Every type of fraud is on the rise, and 2023 was a particularly devastating year for victims of cryptocurrency and…
Kyndryl’s latest State of mainframe modernisation report has found that organisations can achieve as much as a 225% return on…
GitLab has released critical patch updates across its Community Edition (CE) and Enterprise Edition (EE) to address security vulnerabilities and…
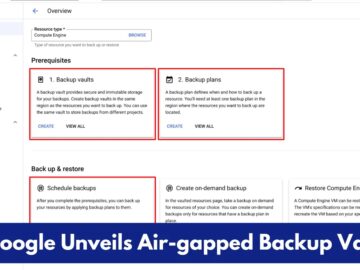
Google Cloud has introduced air-gapped backup vaults as part of its enhanced Backup and Disaster Recovery (DR) service. This new…
The GAZEploit attack consists of two parts, says Zhan, one of the lead researchers. First, the researchers created a way…
SCATTERED SPIDER, a ransomware group, leverages cloud infrastructure and social engineering to target insurance and financial institutions by using stolen…
As ransomware attacks become increasingly sophisticated, hackers are now targeting not just application servers but also their backup systems. This…
VirtualBox is a full virtualizer for x86 hardware designed for servers, desktops, and embedded systems. VirtualBox 7.1 introduces an enhanced…
Sep 12, 2024Ravie LakshmananWeb Security / Content Management WordPress.org has announced a new account security measure that will require accounts…
The UK government has signed the world’s first “legally binding” treaty on artificial intelligence (AI) and human rights, which commits…
TD Bank, one of North American leading financial institutions, has been hit with a hefty fine of $28 million by…
Adobe Patch Tuesday security updates fixed multiple critical issues in the company’s products Pierluigi Paganini September 12, 2024 Adobe addressed…