Thank you for joining! Access your Pro+ Content below. 3 September 2024 The politics of techno-refusal Share this item with…
Transport for London (TfL), the city’s transportation authority, is currently facing an “ongoing cyber incident.” While the incident has not…
The Australian Prudential Regulation Authority (APRA) is set to hire a chief information security officer to “maintain, improve, and manage”…
Image: Midjourney A new ransomware-as-a-service (RaaS) operation is impersonating the legitimate Cicada 3301 organization and has already listed 19 victims on…
In this Help Net Security interview, Tim West, Director of Threat Intelligence and Outreach at WithSecure, discusses Ransomware-as-a-Service (RaaS) with…
India’s cryptocurrency exchange WazirX has revealed that 43% of customer funds lost in a recent cyberattack are unlikely to be…
Hewlett Packard will continue legal proceedings to seek up to US$4 billion ($5.9 billion) in damages from British billionaire Mike…
Transport for London (TfL) is dealing with an ongoing cyberattack Pierluigi Paganini September 02, 2024 Transport for London (TfL) is…
CBIZ Benefits & Insurance Services (CBIZ) has disclosed a data breach that involves unauthorized access of client information stored in…
Hacker ‘HikkI-Chan’ leaks personal data of over 390 million VK users on Breach Forums, including city, country, full names, and…
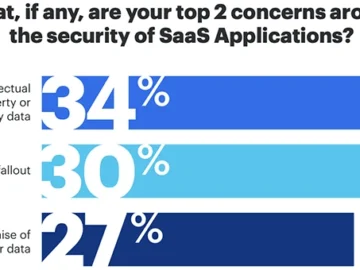
While SaaS security is finally getting the attention it deserves, there’s still a significant gap between intent and implementation. Ad…
Sep 03, 2024Ravie LakshmananInsider Threat / Network Security A 57-year-old man from the U.S. state of Missouri has been arrested…