An Iranian state-sponsored group often referred to as Iran’s Islamic Revolutionary Guard Corps (IRGC) is making headlines again this season…
A sophisticated cyberespionage campaign targeting East Asian countries has been uncovered, with the APT-C-60 group exploiting a zero-day vulnerability in…
The Early Days: Basic Asset Management While it was not called ASM, the concept of managing attack surface management began…
As of August 2024, Iran-based cyber actors continue to exploit U.S. and foreign organizations across multiple sectors. The primary sectors…
Durex India, a se$ual wellness brand that sells condoms and intimate products has fallen prey to a cyber attack leaking…
Aug 30, 2024Ravie LakshmananCryptojacking / Vulnerability Threat actors are actively exploiting a now-patched, critical security flaw impacting the Atlassian Confluence…
Threat actors often target the popular code repository platform “GitHub” due to it’s wide use, and features that this platform…
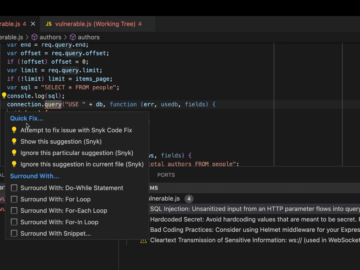
It’s time to give your development process a boost. We’ve all been there staring at a security issue, trying to…
Researchers uncovered a sophisticated phishing campaign that exploits a .NET-based Snake Keylogger variant. This attack leverages weaponized Excel documents to…
I was thrilled to catch up with Blumira during Black Hat USA 2024. When it comes to resource-constrained businesses, traditional…
Aug 30, 2024Ravie LakshmananMalware / Network Security Cybersecurity researchers have disclosed a new campaign that potentially targets users in the…
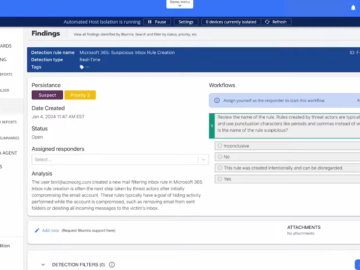
The Communication Challenge in Cybersecurity The vulnerability management process involves various stakeholders, each with their own expertise and communication styles….