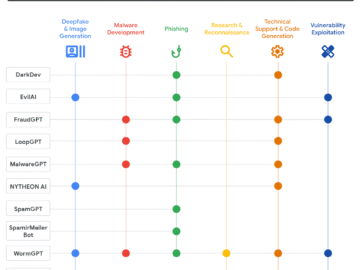
AI malware may be in the early stages of development, but it’s already being detected in cyberattacks, according to new…
QNAP has fixed seven zero-day vulnerabilities that security researchers exploited to hack QNAP network-attached storage (NAS) devices during the Pwn2Own…
The AV-Comparatives Stalkerware Test 2025 delivers a sobering look at the evolving threat posed by stalkerware on mobile devices. Despite…
Nov 07, 2025Ravie LakshmananMobile Security / Vulnerability A now-patched security flaw in Samsung Galaxy Android devices was exploited as a…
Listen to the article 4 min This audio is auto-generated. Please let us know if you have feedback. Dive Brief:…
Federal agencies often collect voluminous amounts of data on Americans to fulfill their missions and better understand the public’s needs. But…
A sophisticated banking trojan named Herodotus has emerged as a significant threat to Android users worldwide. Operating as Malware-as-a-Service, this…
While organisations invest in cyber resilience, the resilience of those leading the charge, chief information security officers (CISOs), is often…
An August ransomware attack against the state of Nevada has been traced to a May intrusion, when a state employee…
A China-linked threat actor has been attributed to a cyber attack targeting an U.S. non-profit organization with an aim to…
The government has announced 14 projects sharing £14m through Innovate UK’s Quantum Sensing Mission Primer awards, to support the development…
A new commercial-grade spyware has apparently been targeting Samsung Galaxy phones in the Middle East, but it’s not clear who’s…