Worldwide end-user cyber security spending is predicted to grow by just over 15% year-on-year over the course of 2025, hitting…
Artificial intelligence (AI) platforms have become integral tools for businesses and organizations worldwide. These technologies promise efficiency and innovation, from…
Texas Dow Employees Credit Union (TDECU) has disclosed that the personal information of over 500,000 members was exposed due to…
28 Aug RaaS Attacks: Economics and Mitigation Strategies Posted at 09:04h in Blogs by Di Freeze This week in cybersecurity…
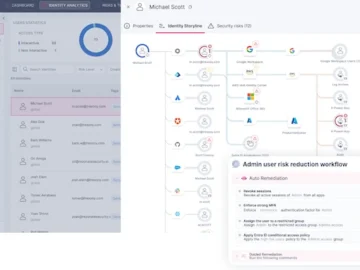
Rezonate announced a new identity security solution for mid-market companies. The offering proactively reduces the identity attack surface and improves…
Security researchers have discovered that the BlackByte ransomware group is actively exploiting a recently patched authentication bypass vulnerability in VMware…
Versa Networks specializes in successful business. It offers Secure Access Service Edge (SASE), consolidating networking and security services in a…
Virtual private networks (VPNs) have been the workhorse of secure remote access for decades. They offer a seemingly simple solution:…
Web3’s growth demands strong infrastructure. Discover how decentralized security, verified data, and distributed AI are revolutionizing the industry. From DeFi…
Organizations using Fortra’s FileCatalyst Workflow are urged to upgrade their instances, so that attackers can’t access an internal HSQL database…
Cambridge Enterprise has saved tens of thousands of pounds and freed up administrators to do more productive work after switching…
US offers $2.5M reward for Belarusian man involved in mass malware distribution Pierluigi Paganini August 28, 2024 The US Department…