IBM has issued a security bulletin addressing critical vulnerabilities in its MQ Operator and Queue Manager container images. These vulnerabilities,…
Progress Software has released an emergency patch for a critical 10/10 severity vulnerability (CVE-2024-7591) in its LoadMaster products, allowing remote…
Sep 09, 2024Ravie LakshmananCyber Espionage / Malware The China-linked advanced persistent threat (APT) group known as Mustang Panda has been…
As founder Larry Ellison made final tweaks to his keynote speech at Oracle’s annual CloudWorld fest in Las Vegas, the…
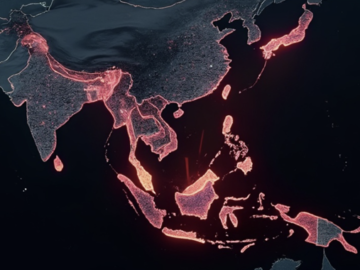
Earth Preta, a notorious threat group, has been observed upgrading its attacks to distribute malware via removable drives, employing a…
The US Commerce Department is proposing to require detailed reporting requirements for advanced artificial intelligence developers and cloud computing providers…
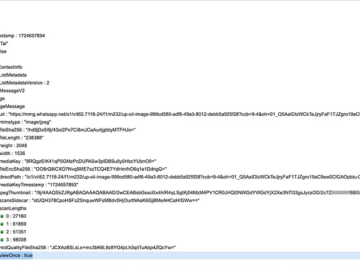
Experts demonstrated how to bypass WhatsApp View Once feature Pierluigi Paganini September 09, 2024 Users are exploiting a privacy flaw…
Ransomware affiliates exploit a critical security vulnerability in SonicWall SonicOS firewall devices to breach victims’ networks. Tracked as CVE-2024-40766, this improper…
The NSA, FBI, CISA, and allies have assessed the cyber actors associated with the Russian General Staff Main Intelligence Directorate…
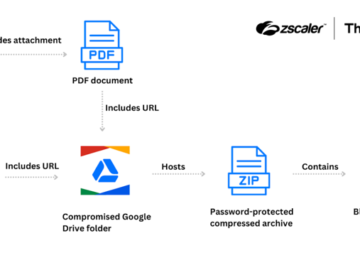
Critical vulnerabilities have been identified, potentially exposing systems to arbitrary command execution. These vulnerabilities, cataloged under the Common Vulnerabilities and…
Sep 09, 2024Ravie LakshmananFinancial Security / Malware The Colombian insurance sector is the target of a threat actor tracked as…
Interview: Jon Grainger, CTO, DWF Source link