With all the recent hype, many may not realize artificial intelligence is nothing new. The idea of thinking machines was…
26 Aug Most Businesses Unprepared for a Ransomware Attack Posted at 08:53h in Blogs by Di Freeze This week in…
Deniss Zolotarjovs, 33, from Moscow, Russia, was charged with federal crimes in the U.S. District Court in Cincinnati today. A…
Patelco Credit Union has disclosed a ransomware attack that compromised the personal data of its members and employees. The breach,…
Aug 26, 2024The Hacker NewsData Security / Compliance Nowadays, sensitive and critical data is traveling in everyday business channels that…
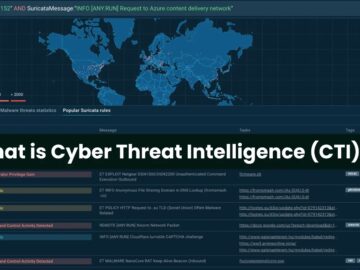
Cyber Threat Intelligence (CTI), also known as Threat Intelligence or Threat Intelligence, is a critical practice in cybersecurity. It involves…
New research reveals critical vulnerabilities in Python applications for Windows including Snowflake, Gradio, Jupyter, and Streamlit that could allow hackers…
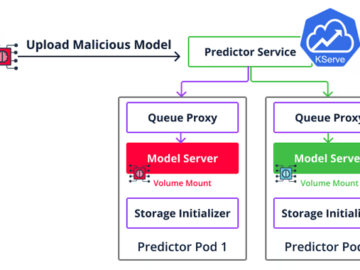
Cybersecurity researchers are warning about the security risks in the machine learning (ML) software supply chain following the discovery of…
Threat actors successfully deployed BlackSuit ransomware after maintaining access to a compromised network for 15 days. The intrusion, which began…
Argentine authorities have arrested a Russian national accused of laundering cryptocurrency payments linked to the notorious North Korean Lazarus Group….
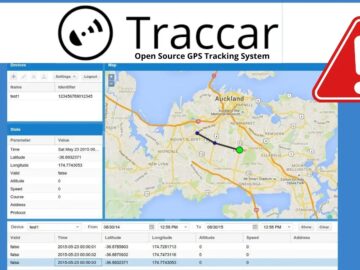
Two critical vulnerabilities have been discovered in the Traccar GPS. These vulnerabilities, CVE-2024-31214 and CVE-2024-24809, allow unauthenticated attackers to execute…
Security researchers have recently identified a new malware strain that employs advanced obfuscation techniques to evade detection by antivirus software….