Ransomware affiliates exploit a critical security vulnerability in SonicWall SonicOS firewall devices to breach victims’ networks. Tracked as CVE-2024-40766, this improper…
The NSA, FBI, CISA, and allies have assessed the cyber actors associated with the Russian General Staff Main Intelligence Directorate…
Critical vulnerabilities have been identified, potentially exposing systems to arbitrary command execution. These vulnerabilities, cataloged under the Common Vulnerabilities and…
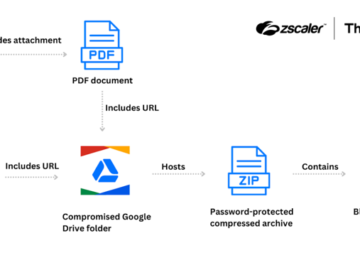
Sep 09, 2024Ravie LakshmananFinancial Security / Malware The Colombian insurance sector is the target of a threat actor tracked as…
Interview: Jon Grainger, CTO, DWF Source link
James Cook University is pursuing a digital refresh and a new cyber security strategy under new digital leadership. JCU The…
At HackerOne, SDRs focus on prospecting, qualifying leads, and setting up meetings for AEs, while developing these skills to take on…
Highline Public Schools, a K-12 district in Washington state, has shut down all schools and canceled school activities after its…
As a business owner, you’ve likely invested in various security tools such as SIEMs, antivirus software, and IDS/IPS systems. You…
As the new school year begins, students are gearing up for new classes and friendships and diving back into the…
Sep 09, 2024Ravie LakshmananVulnerability / Hardware Security A novel side-channel attack has been found to leverage radio signals emanated by…
Over 2,000 victims of the Post Office Horizon scandal can now appeal the financial redress they have received if they…