A Go-based command-and-control (C2) framework originally marketed within Chinese-speaking offensive security communities has been quietly expanding its reach, drawing growing…
The Cybersecurity and Infrastructure Security Agency on Thursday warned that a malware variant previously used in attacks against Ivanti Connect…
It has been a whirlwind few months for Peter Steinberger and his creation, OpenClaw. The AI tool, which acts as…
Ravie LakshmananFeb 27, 2026Malware / Linux Security Cybersecurity researchers have disclosed details of a malicious Go module that’s designed to…
Listen to the article 6 min This audio is auto-generated. Please let us know if you have feedback. The Trump…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has released new details about RESURGE, a malicious implant used in zero-day…
When security teams talk about attack surface, the conversation usually starts in familiar places. Servers, identity systems, VPN access, cloud…
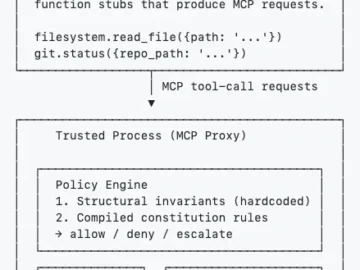
Veteran security engineer Niels Provos is working on a new technical approach designed to stop autonomous AI agents from taking…
The UK is losing its leadership in open banking, having “laid the rail track, but hesitated to run the trains”,…
Malicious Go Crypto Module Steals Passwords and Deploys Rekoobe Backdoor in Developer Environments A newly discovered supply chain attack is…
A new backdoor dubbed Dohdoor is actively targeting schools and health care organizations in the United States through a stealthy multi-stage attack…
Cybercrime Magazine’s latest YouTube Short video, produced by Taylor Fox, looks back at a riveting privacy and surveillance story that gripped…